Hi again,
Welcome my first bug bounty write up, I don't do bug bounty that much especially web bug bounties but it started to interest me lately so I decided to start looking for bugs in UBER.
Disclaimer
Before you start I highly recommend you read about SAML authentication if you are not already familiar with the topic, otherwise, it will be really hard to understand the bug.
You can read about SAML Here
Information Gathering
I started gathering information about the target, I noticed that their internal systems are in scope (subdomains of uberinternal.com), so I started performing subdomain enumeration, For that, I used aquatone which discovered a number of domains and gathered some screenshots of the domains.
One thing to notice was that most of the internal domains redirect to uber.onelogin.com for the authentication process.
onelogin is known to use SAML authentication which is very interesting because of a large number of authentication bypasses discovered in applications implementing SAML, including some bugs affecting uber itself which you can find Here and Here.
My first intention was to look for SAML authentication bypasses, and believe it or not, I was going to start with the uchat system but sadly someone got the bug first, this is not the first time I lost a bug because of bad timing so it's OK .. let's move on.
When you log in with SAML a request is sent to the authentication service, in our case this is uber.onelogin.com and after the login uber.onelogin.com will send back a response in case of successful login to the application which in this case whatever.uberinternal.com what I was interested in finding was the page that receives the response from onelogin.
So let's take a look at the redirection that happens when calling a page that requires authentication, you can see in the following image that it passes a SAMLRequest base64 parameter to uber.onelogin.com.
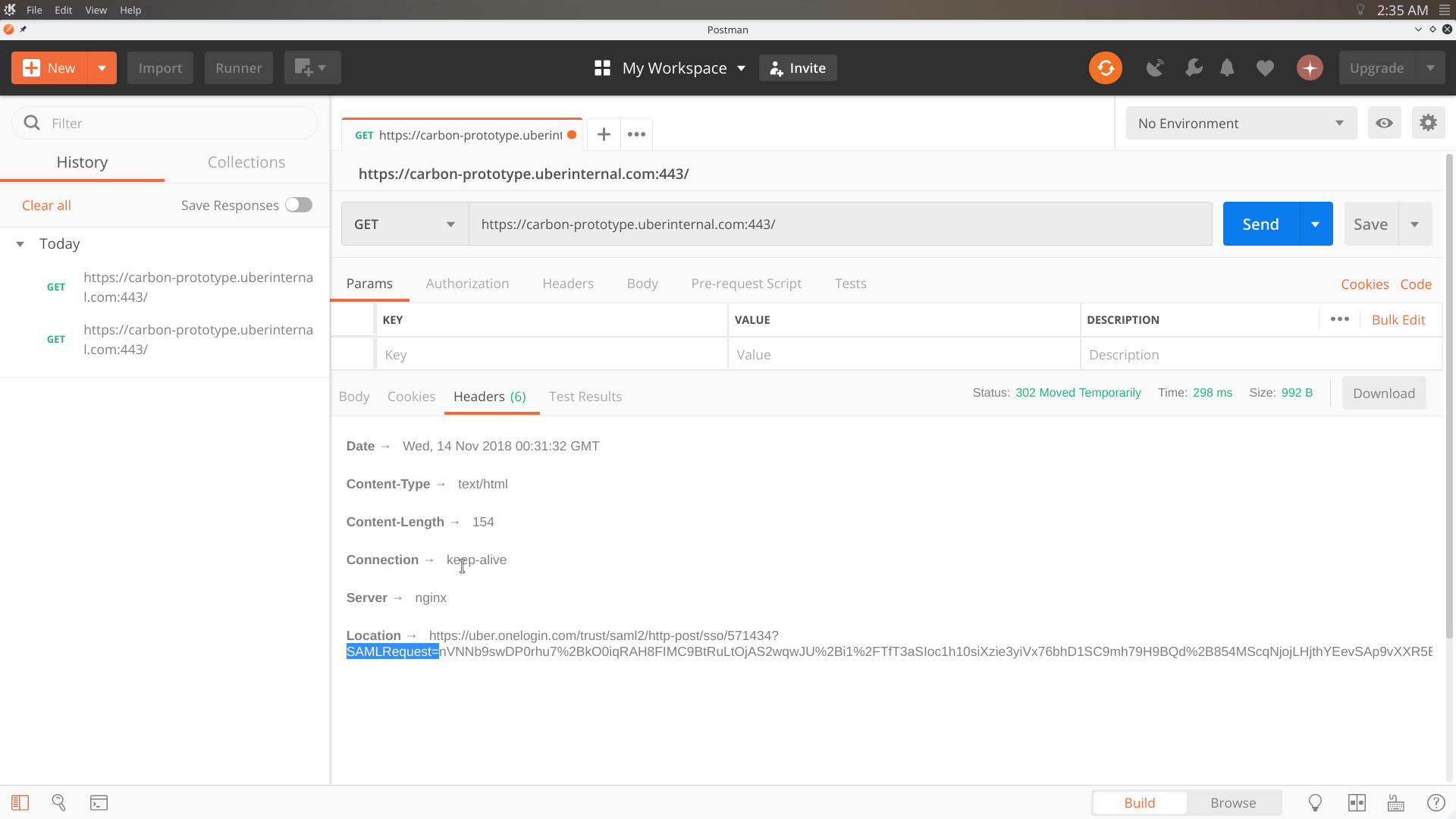
To decode the value of the parameter there exists an online tool that allows us to do just that and we can see the link that will receive the response from uber.onelogin.com 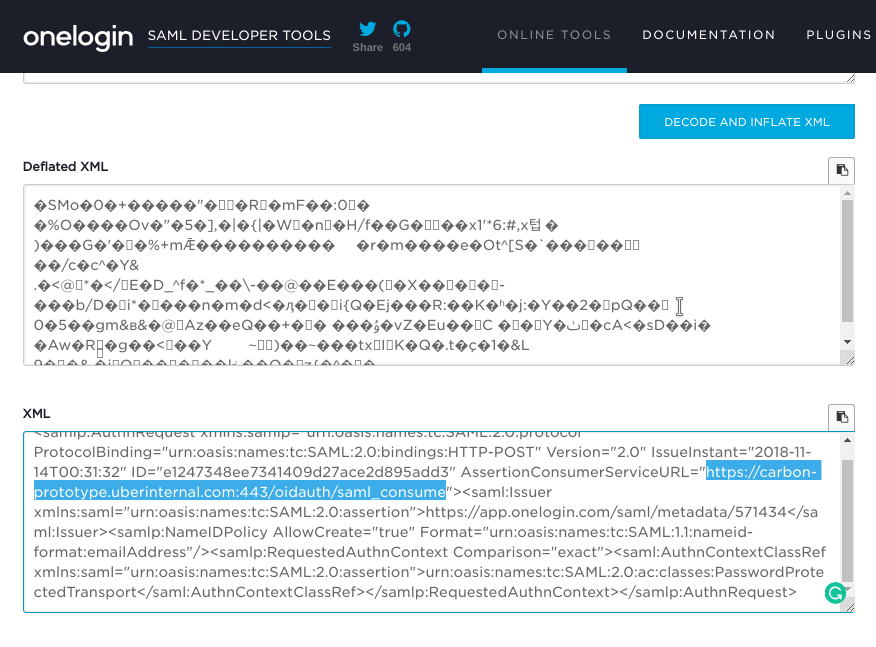 .
.
Also, there's a good SAML plugin for burpsuite if you want to give it a try, also it has some really good advanced features to test SAML.
That was OK, however, I wanted to do that in bulk, so I created a tool that takes a list of URLs and gives back the SAML consuming URL, you can find the tool here in my GitHub account SAMLExtractor.
The next thing was to try to bypass SAML authentication on that link but I didn't have luck with that so I decided to do something else, I decided to do some discovery of the oidauth/ directory to see if there are any more interesting files, for that I used dirsearch using the following command.
./dirsearch.py -u https://carbon-prototype.uberinternal.com:443/oidauth/ -ejson
The Bug
After performing the directory brute forcing I found the following page:
https://carbon-prototype.uberinternal.com:443/oidauth/logout
It's a logout page but why that's interesting .. well a lot of developers implement a redirection in the logout page and sometimes you can find XSS vulnerability in there so I opened the above link and it did redirect me to the following page
https://carbon-prototype.uberinternal.com/oidauth/prompt?base=https%3A%2F%2Fcarbon-prototype.uberinternal.com%3A443%2Foidauth&return_to=%2F%3Fopenid_c%3D1542156766.5%2FSnNQg%3D%3D&splash_disabled=1
The base parameter is taking a URL so how about replacing that with the old classic javascript:alert(123); to see if it can trigger an XSS and it did by clicking the link that appears in the page, and because the page was also vulnerable to clickjacking it means you can combine both in your attack scenario (this is explained in detail in the report).
Mass Exploitation
Remember when I told you I created a tool that can take a list of URLs and then give you back the callback (SAML consume) URL, I decided to feed the tool with all subdomains of uberinternal.com to see if there are other domains that use the same library and there was.
What I did next was to create a script that calls the vulnerable page oidauth/prompt and try the XSS and if my input is reflected it gives me a nice vulnerable message.
import requests
import urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
from colorama import init ,Fore, Back, Style
init()
with open("/home/fady/uberSAMLOIDAUTH") as urlList:
for url in urlList:
url2 = url.strip().split("oidauth")[0] + "oidauth/prompt?base=javascript%3Aalert(123)%3B%2F%2FFady&return_to=%2F%3Fopenid_c%3D1520758585.42StPDwQ%3D%3D&splash_disabled=1"
request = requests.get(url2, allow_redirects=True,verify=False)
doesit = Fore.RED + "no"
if ("Fady" in request.content):
doesit = Fore.GREEN + "yes"
print(Fore.WHITE + url2)
print(Fore.WHITE + "Len : " + str(len(request.content)) + " Vulnerable : " + doesit)
After that, I verified the vulnerable pages and sent the first report to UBER, and after the first report, I found more two vulnerable subdomains which I reported in a separate report.
Links to the reports:
Reflected XSS on multiple uberinternal.com domains
Reflected XSS in https://eng.uberinternal.com and https://coeshift.corp.uber.internal/
Bounty:
- First Report
2k$ - Second Report
500$